Microsoft has successfully taken a court order out on six domains that were engaged in phishing operations against Office 365 subscribers. With the order, the company was able to take control of the domains, which often used COVID-19 to lure unwitting users.
As reported by ZDNet, the phishing campaign has been happening since December 2019 but later leveraged the COVID-19 pandemic as an attack method. Bad actors would send emails to Office 365 account holders design to look like they came from their employer or co-workers.
Microsoft describes the campaign as unique because it used a rare attack method. Usually, phishing attacks will attempt to redirect users to a nefarious website designed to look official. In this case, that would have meant a website that looked like an Office 365 page.
However, this attack instead prompted users to open an Office document. Microsoft says users who tried to open the document would be sent to an install for a third-party Office 365 application. This app was created by the attack group and was loaded with malware.
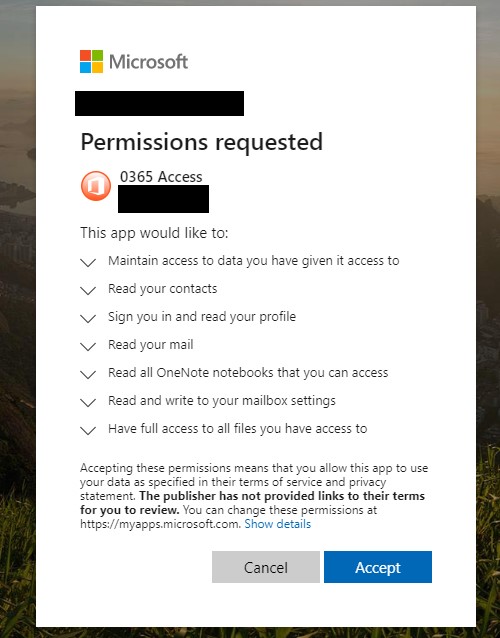
Any users that went through the process and installed the app would put their machine at risk. In fact, the bad actors could gain access to their whole Microsoft accounts, including files, contacts, emails, settings, and more.
Attack
Microsoft says attacks that worked were successful because of three reasons:
- The hackers created an accurate app that looked like it was from Microsoft.
- Because Office 365 promotes integrated apps, enterprise users are inclined to install such apps when prompted.
- Importantly, the group used a trick to send users to the official Microsoft account login page. When the user signed in, the hackers would redirect them to the malicious app.
While this was a relatively sophisticated phishing campaign, Microsoft believes it was perpetrated by two people. In a blog post, Tom Burt, Corporate Vice President, Customer Security & Trust at Microsoft, said the end goal seems to be to follow up with BEC attacks.
“This malicious activity is yet another form of business email compromise (BEC) attack, which has increased in complexity, sophistication and frequency in recent years. According to the FBI's 2019 Internet Crime Report, the most-costly complaints received by their Internet Crime Complaint Center (IC3) involved BEC crimes, with losses of over $1.7 billion, representing nearly half of all financial losses due to cybercrime.”
Last Updated on September 14, 2020 4:24 pm CEST by Luke Jones






