Back in June, Microsoft first announced their partnership with Lookout to bring their Mobile Enterprise and Security suite to EMS. Since then the two companies have been hard at work, and the functionality is now generally available.
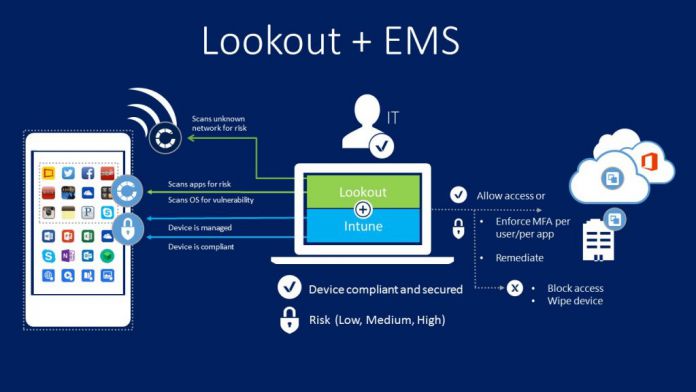
Lookout pulls telemetry data from 100 million phones and analytics from over 30 million apps. The service then uses this data, as well as static and behavioral analysis to detect malware in apps and devices. Furthermore, Lookout can use its analysis to detect new threats which have never been seen before and prevent them.
Enterprise Mobility Suite and Lookout Mobile Enterprise Security Features
The combination of the two services results in some powerful tools, listed for you below:
- “Allow access from devices to corporate e-mail only if the risk score is “Secured” or “Low.”
- Not synchronize corporate files to a device if its risk score is “High.”
- Not allow access to any corporate assets if Lookout's app is not running on the device and/or properly reporting device health. It will then automatically guide users to download and activate Lookout's app.
- Enforce a policy to deny access for a specific group of business critical apps when devices are not compliant to Lookout. General purpose LoB apps, however, would not be restricted.
- Selectively allow access to a primary collection of apps regardless of risk, while restricting access to a secondary list of apps when risk score is “Secured” or “Low.”
- Receive alerts when “High” risk devices are detected in their environments.
- Automatically trigger Lookout's self-remediation flow when devices are non-compliant or “High” risk to them block from accessing corporate resources.
- Retire or wipe a device when it becomes “High” risk.
- The service integration here is seamless to our enterprise customers leveraging the assets of EMS to enable unified device and user (both end-user and IT Professional) identity through Azure Active Directory.”
You can enable and manage Lookout right now, directly from the Intune console. Admins can choose between different configurations to ensure that privacy matches the standards of various organizations.
You can find out more about the integration on the TechNet blog, or read the whitepapers for an in-depth explanation of Lookout.