Microsoft has confirmed a serious zero-day vulnerability in its Exchange email server. Known as PrivExchange, the flaw lets a regular exchange user utilize python scripts to remotely gain administrator privileges.
In its security advisory, Microsoft acknowledged the issue and provided several temporary workarounds.
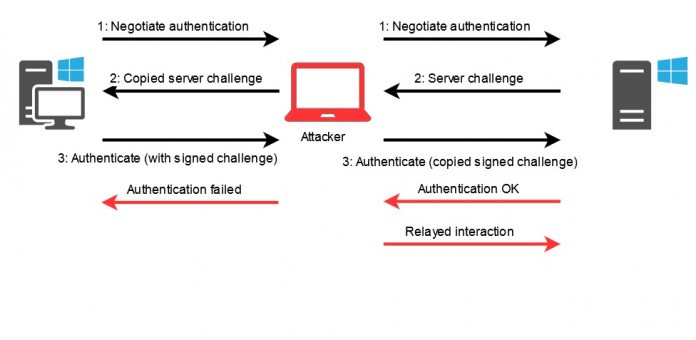
“An elevation of privilege vulnerability exists in Microsoft Exchange Server. An attacker who successfully exploited this vulnerability could attempt to impersonate any other user of the Exchange server,” said the company. “To exploit the vulnerability, an attacker would need to execute a man-in-the-middle attack to forward an authentication request to a Microsoft Exchange Server, thereby allowing impersonation of another Exchange user.”
A Three-pronged Issue
PrivExchange was first brought to light by Fox-IT’s Dirk-jan Mollema late last month. According to the researcher, the issue is a result of three vulnerabilities working together:
- The default Exchange Web Services (EWS) feature gives attackers the ability to manipulate servers, allowing them to authenticate a bad actor through a hacked email account.
- To achieve this, the attacker uses NTLM hashes sent through HTTP, while the server will also not set Sign and Seal flags on the NTLM operation. Essentially, this means the NTLM authentication is left open to attack. Bad actors can then obtain the hash.
- Microsoft Exchange servers allow access to sensitive operations by default. Typically, only company admins have access to servers and the higher privileges, normal email account holders do not. However, with elevated access, the attackers can gain access to the Domain Controller and grant themselves access to sensitive material. Furthermore, the attack will allow the ability to create more backdoor accounts.
Due to the complexity of the issue, it will likely take a while for Microsoft to craft a fix. On-premises installs can mitigate the issue by disabling NTLM. You can find more information about mitigations here.