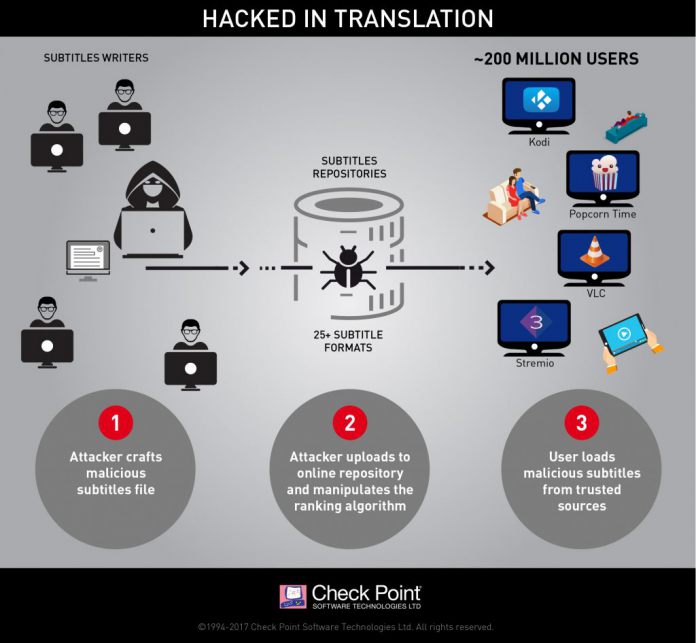
Earlier this week, security firm Check Point published a report about a rare type of attack that could affect millions of Windows systems. The exploit allows attackers to inset malware onto subtitle files within numerous media players. Check Point has now updated its blog post to reflect which media players have been fixed.
If you missed the original problem, the firm pointed out that media players like VLC, Popcorn Time, Stremio, and Kodi. In its first post, Check Point showed that around 200 million streamers using the various vulnerable services.
It is worth noting that these are four of the most used media players, so the potential for users to be affected is huge. In the updated situation, Check Point has confirmed two of the media players have now been fixed. However, two remain vulnerable:
- PopcornTime– Created a Fixed version, however it is not yet available to download in the official website.
The fixed version can be manually downloaded via the following link: https://ci.popcorntime.sh/job/Popcorn-Time-Desktop/249 - Kodi– Created a fix version, which is currently only available as source code release. This version is not yet available to download in the official site.
Link to the source code fix is available here: https://github.com/xbmc/xbmc/pull/12024 - VLC– Officially fixed and available to download on their website
Link: http://get.videolan.org/vlc/2.2.5.1/win32/vlc-2.2.5.1-win32.exe - Stremio– Officially Fixed and avilable to download on their website
Link: https://www.strem.io/
“Some of the issues were already fixed, while others are still under investigation. To allow the developers more time to address the vulnerabilities, we've decided not to publish any further technical details at this point.”
New Infection
The discovery is worrying because subtitle files are very common on media files. Furthermore, companies that offer media playing services view these subtitles as a trusted source.
Check Point says security protocols, such as anti-virus, also typically overlook these files. Subtitles are usually viewed as harmless tech files by security program, allowing malware to potential pass undetected.
“The attack vector relies heavily on the poor state of security in the way various media players process subtitle files and the large number of subtitle formats. To begin with, there are over 25 subtitle formats in use, each with unique features and capabilities.”
Because of this easy access, attackers can take complete control over a device running the file. The malware can help hackers to shut down a machine, spy on its, or steal information. Check Point describes the potential damage as “endless”.