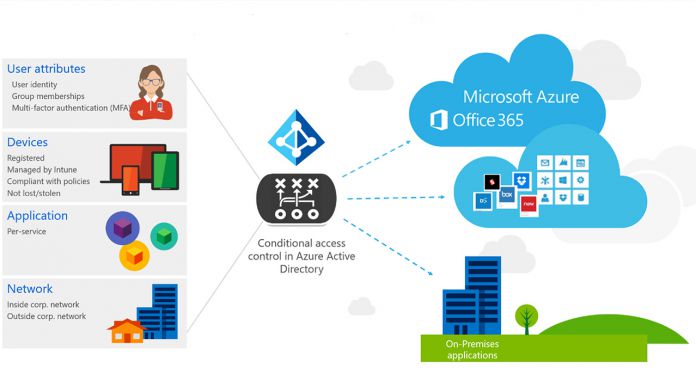
The Enterprise Mobility and Security (EMS) team has been quite busy recently, adding several improvements to Conditional Access and implementing it in the Azure portal.
The improvements include risk-based access policies per application, greater flexibility to protect applications and a unified administrative experience on the Azure portal.
Details on the new improvements are described in the official blog post:
- Risk-based access policies per application. Leverage machine learning on a massive scale to provide real-time detection and automated protection. Now you can use this data to build risk-based policies per application.
- Greater flexibility to protect applications. Set multiple policies per application or set and easily roll out global rules to protect all your applications with a single policy.
- All these capabilities are now available in a unified administrative experience on the Azure portal. This makes it even easier to create and manage holistic conditional access policies to all your applications.
Identity-driven security
Conditional Access also allows users to determine certain policies. These are simple statements about when you should apply one (called Conditions) and what action or requirement should follow it (Controls).
Image credit: Microsoft
They provide efficient management at multiple levels, such as the user, location, device, and app levels. Because of these policies, you can allow or block access to certain users. You can also challenge users with features like multi-factor authentication, device enrollment, or a simple password change.
In addition, Conditional Access also takes risk information into consideration, thanks to Microsoft's Intelligent Security Graph. The latest, improved capabilities offer more flexible and powerful policies for a more efficient productivity while protecting data.
Due to the nature of online access, users have a large number of devices at their disposal for connecting. As such, conditions often change and setting adequate policies makes sure you get the full control and protection while allowing work from any device. Therefore, only the right users on compliant devices are able to access sensitive data.
Detailed information on these new capabilities is available here.