All Firefox users should immediately switch to a different secure browser until the fix arrives. The vulnerability allows an attacker to execute code on user's Windows workstation.
The exploit is in the wild, meaning it's now in the public domain and every hacker has access to it. So far, there is no fix available.
All the information points that this is a watering hole attack. In order for it to be effective, a victim has to visit a certain website that contains the exploit code.
Furthermore, this exploit causes an affected workstation to report back to an IP address 5.39.27.226, a web server hosted at OVH in France. However, the site is now down.
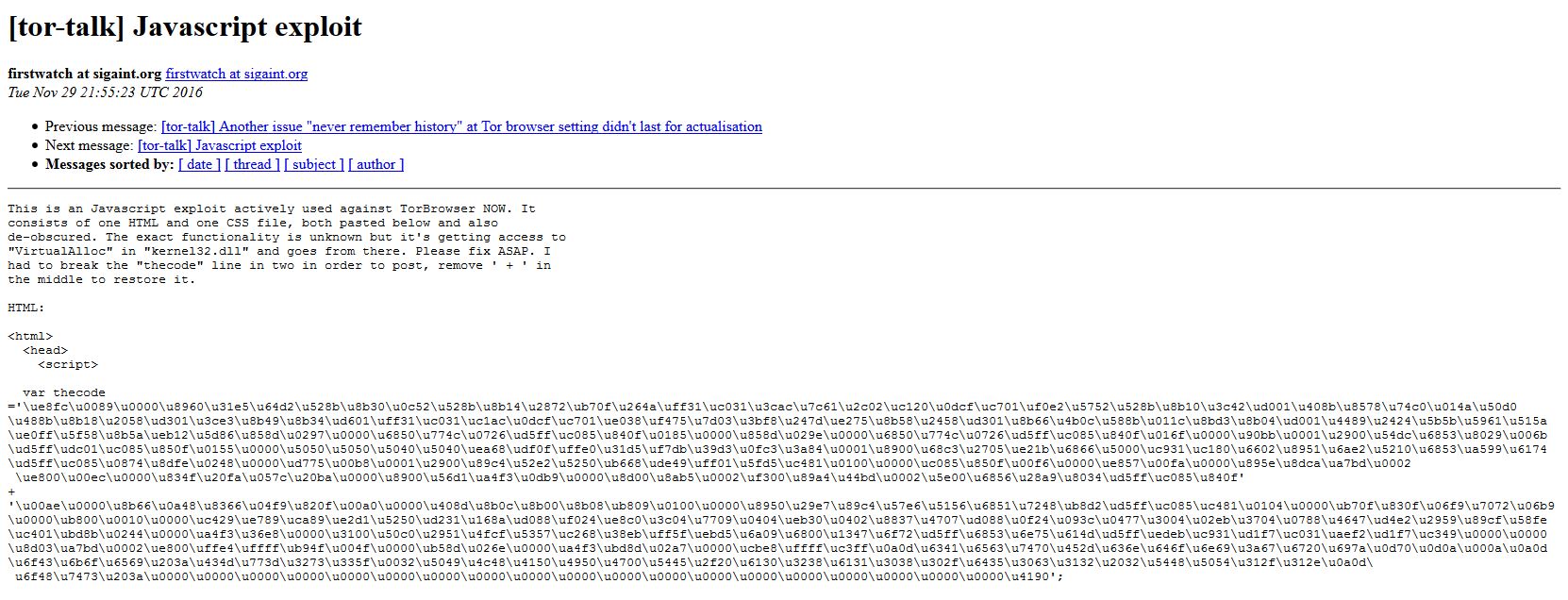
The exploit first popped up in a post on the official Tor website. It shows lines in JavaScript and an introduction that says it's the JavaScript exploit used against the Tor browser.
Similarities with an another attack
The shellcode (code that executes on your Windows workstation once exploited) is very similar to the shellcode used by the FBI back in 2013 to deanonymize visitors to child porn websites hosted by FreedomHosting.
An independent researcher, known as @TheWack0lian on Twitter, first noticed the similarities between the two. He said that “most of the code is identical, just small parts have changed.”
The shellcode used is almost exactly the shellcode of the 2013 one https://t.co/6vuIzqp0rj
…except it builds sockaddr_in on the stack. https://t.co/pWsUe4uHiZ
— slipstream/RoL (@TheWack0lian) November 29, 2016
The malicious payload that the exploit delivers is the same in both cases. Specifically, a memory corruption vulnerability allows execution of the malicious code on computers running Windows.
Considering that the exploit code is now public knowledge, new variants of this attack are likely to show up. As a result, there is a high probability the code will be repurposed to infect workstations with malware or ransomware.
A representative of Mozilla told Ars Technica they were aware of the vulnerability and are working on a fix. Firefox users should at the very least disable JavaScript on as many sites as possible if they are currently unable to switch to a secure browser.
We will keep you posted on further development regarding this incident.