Redmond is continuing its fight against Ransomware and has written an extensive post that goes in-depth on the current situation regarding the increasingly popular malware method.
Microsoft has given an in-depth look at the current situation with ransomware and the threat this type of attack brings to users.
Ransomware is the kind of malware that does exactly what it says on the tin, taking over files or whole systems through encryptions and then holding users to ransom.
The only way to unlock the infected files is to pay the ransom, which does not always result in the attacker lifting the encryption.
Microsoft says the industry is becoming more alert to ransomware as it has increasingly been used in large-scale attacks, and is not merely affecting users at a consumer level.

In its extensive blog post, the company offers an example of ransomware (above) and highlights some of the classic examples of ransomware:
“ Make encrypted data unrecoverable after a certain period of time
Threaten to post captured (potentially sensitive) data publicly
Use fear by claiming to be law enforcement and threaten prosecution
Increase the ransom payment amount as time goes on
Render the machine unbootable when it overwrites the Master Boot Record and encrypts physical sectors on disk
Threaten to erase all data and render all enterprise computers inoperable”
Microsoft says it has been tackling ransomware for some time and has covered the malware extensively in volumes of the Microsoft Security Intelligence Report. With industries and large enterprise organizations now at risk, Microsoft says now is the time for CISOs, risk managers, and security companies to understand ransomware and its risks.

During the first quarter of 2015, the ER (encounter rate) for ransomware was 0.35 percent (above), while in the second frame of last year it was 0.16 percent. The data shows that Trojans are still posing more of a risk compared to ransomware, with the ER for Trojans sitting at 3.92 percent (Q1) and 4.45 percent (Q2) in 2015, up to 28 time higher than the ER for ransom attacks.
Microsoft points out that ransomware is still relatively rare compared to other types of attack, such as viruses, Trojan Downloaders & Droppers, and most other attacks. However, while globally ransomware continues to be a statistically minor threat, in certain countries it is on the rise and ignoring it will simply not be enough anymore.
The industry must prepare for a rise in ransomware Microsoft argues as more threats are targeting major industries and organizations.
“Although the global encounter rate is just a fraction of a percent, there are some countries/regions that have higher encounter rates. i.e. the probability of encountering ransomware is higher in some locations than others. For example, the ER in Mexico was 5 times higher at 0.8 percent during the same period. France and Canada had ransomware encounter rates 4.4 times higher than the worldwide average at 0.7 percent, while the United States, Russia and Turkey all had elevated ransomware encounter rates, 3.75 times higher than the worldwide average, at 0.6 percent.”

As you can see in the image above, counties like Italy and the UAE have the highest rates of ransomware attacks, but even so the threat is statistically minimal compared to other types of malware. The reason for the low ER is that most systems that run the Windows Malicious Software Removal Tool (MRST) also have current anti-virus protection.
Most modern anti-virus services that are up to date can block against known commodity ransomware and stop a system becomes infected.
Measuring malware infections is done on the Computers Cleaned per Mille (CCM) measurement, which takes into account the number of machines cleaned for every 1,000 unique users that use MRST.
“For example, if MSRT has 50,000 executions in a particular location in the first quarter of the year and removes infections from 200 computers, the CCM for that location in the first quarter of the year is 4.0 (200 ÷ 50,000 × 1,000).
Detection for new malware families are typically added to the MSRT every month. The MSRT cleans many of the most prevalent families of ransomware like Win32/Crowti, Ransom: Win32/Reveton, and Win32/Samas. Of these, Crowti had the highest CCM in the second half of 2015, 0.04 in 3Q15 and 0.01 in 4Q15. This means that for every 1,000 systems the MSRT executed on in the fourth quarter of 2015, 0.01 was cleaned of Crowti; that’s 1/1000 of a percent of the hundreds of millions of systems the MSRT executes on each month.”
While ransomware represents a lower ER risk compared relatively to other types of malware, the strategy is rising in popularity among attackers. Increasing use of social media, USB drivers, and Email means these are the main methods by which hackers access systems to offload the malware encryptions.
Redmond also reveals that the rising popularity of this attack has invited a more open “market” which means even less-skilled attackers a learning to stage functional ransomware packages. This has been exacerbated by darkweb, Sarento, and Enrume offering ransomware-as-a-service (RaaS) to attackers.
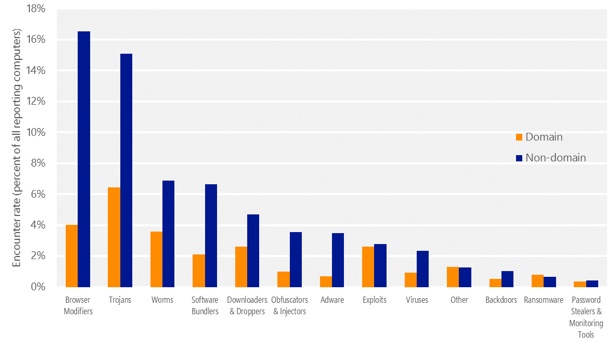
Couple ransomware with other types of malware (above), most notably exploit kits like Angler, is giving attackers more options for entering a system and then encrypting it.
Microsoft says the easiest entry point for attackers is through internet facing servers, allowing even large-scale organizations to fall to file or whole system encryptions. In terms of industry, this means locking down critical data, which is achieved by accessing IT infrastructure and exploiting weak passwords to enter systems.
Microsoft urges users and industries to ensure their data is sufficiently backed up and warns that not backing up could result in huge financial cost and the loss of valuable data.
It is worth heading the source to read Microsoft’s blog post in full, which goes into the finer details of the current situation with ransomware.